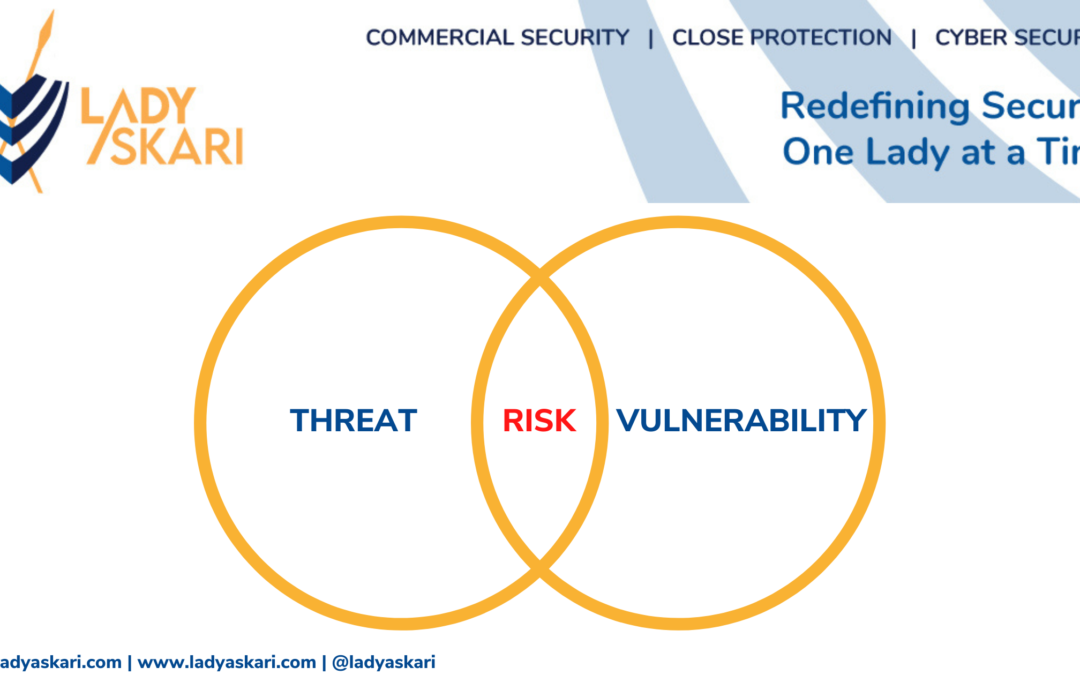
Oftentimes people and/or organizations outside the security industry, and sometimes even security professionals mix up the terminology of threat, vulnerability and risk. It is crucial to understand the relationships between threats, vulnerabilities and risks to build effective security policies and keep your organization safe from various cyber and physical attacks.
We want to highlight the differences in definitions of threats, vulnerabilities, and risks within the context of security;
Threat
A threat is anything that has the potential to disrupt or do harm to an organization. Threats can be natural, intentional or unintentional. Natural threats are hazards such as earthquakes, floods and wildfires, which are random in terms of duration and impact. Intentional threats are actions done on purpose like to steal or damage computer resources, equipment, and data. Unintentional threats are attributed to human error, e.g. leaving the door to IT servers unlocked, or leaving the front door of the organization containing sensitive information unmonitored.
Vulnerability
A vulnerability is a weakness or gap in a security system, which can be exploited by threat actors in order to achieve their goals. A vulnerability assessment is a systematic review of weaknesses in a security system and evaluates if the system is susceptible to any known vulnerabilities, it should assign severity levels to those vulnerabilities, and then recommend remediation or mitigation, if and whenever needed. Vulnerabilities show themselves via several avenues:
- Current employees: Social interaction, customer interaction, discussing work in public locations, taking data out of the office (e.g phones, laptops), emailing documents and data, installing unauthorized software and apps, opening spam emails, connecting personal devices to office networks, writing down passwords and sensitive data, losing security devices such as ID cards, lack of information security awareness.
- Former employees: Those who are working for competitors, retaining company equipment and data, or discussing company matters.
- Technology: Social networking, file sharing, saving data on mobile devices such as mobile phones, Internet browsers, computers or other devices.
- Partners and suppliers: Disruption of telecom services and utility services such as electric, gas, water, hardware and software failure, lost mail and courier packages, supply disruptions, sharing confidential data with partners and suppliers
- Security Systems: Faulty cameras, sensors, or other security devices. Broken or unfollowed security policies or procedures.
While most organizations implement some type of security, hardly any consider the numerous security weaknesses that exist in their current circumstance. You ought to consider physical security, report the weaknesses in your environment, and make business choices about how to keep those weaknesses from compromising the security of your organization.
Risk
A risk is the effect of uncertainty on objectives. It’s usually expressed in terms of risk sources, potential events, their consequences and their likelihood.
A risk assessment is the overall process of risk identification, risk analysis and risk evaluation. Organizations should invest in a risk assessment program to better understand, measure and prepare for risks to their operations. A risk assessment involves evaluating not only the physical site but also how business is done which could create additional threats and vulnerabilities. These assessments offer numerous benefits including;
- Helping to identify which parts of your security measures are weak and what security threats face your organization. This enables you to address vulnerabilities and enhance your company’s security.
- See if your organization’s security measures meet the requirements put in place by the government / international bodies.
- Enable you to have a clear vision of how efficient your security controls are and how you can upgrade them.
Remember, risk does not end once the basic security systems have been put in place. Risk assessments should take place regularly as threats and vulnerabilities are constantly changing and a risk assessment is like a snapshot of the current risk. A well planned risk assessment program will save your organization from undesirable losses.